- AWS Direct Connect links your internal network to an AWS Direct Connect location over a standard Ethernet fiber-optic cable. One end of the cable is connected to your router, the other to an AWS Direct Connect router. With this connection, you can create virtual interfaces directly to public AWS services (for example, to Amazon S3) or to Amazon VPC, bypassing internet service providers in your network path
- Low latency,
low jitter, non-internet – all traffic over AWS backbone
- AWS Direct Connect locations available throughout the world
- customer Router must support
802.1Q (networking standard that supports virtual LANs (VLANs) on an IEEE 802.3
Ethernet network, see below)
- BGP only, no manual route
configuration
VIF - Virtual Interface:
- This is the doorway into Direct Connect: You can create a private Virtual
InterFace to connect to your VPC via DirectConnect. Or, you can
create a public virtual interface to connect to AWS services that aren't
in a VPC, such as Amazon S3 and Glacier. For private virtual interfaces,
you need one private virtual interface for each VPC to connect to from the AWS
Direct Connect connection, or you can use a AWS Direct Gateway (see below)
Direct Connect Gateway (aka VIF - Virtual Interface):
- https://docs.aws.amazon.com/directconnect/latest/UserGuide/direct-connect-gateways.html
- You must create one of the following virtual interfaces to begin using your AWS Direct Connect connection:
- You must create one of the following virtual interfaces to begin using your AWS Direct Connect connection:
- Private
- REGIONAL - allows to connect to a VPC in the SAME region. 1 per VPC
- should be used to access an Amazon VPC using private IP
addresses
- Public
– connect to public AWS end point in ANY region
- A public virtual interface can access all AWS public services
using public IP addresses.
- 802.1Q – can have up to 4096 channels on AWS trunk
- Transit
- A transit virtual interface is
a VLAN that transports traffic from a Direct Connect gateway to one or more
transit gateways.

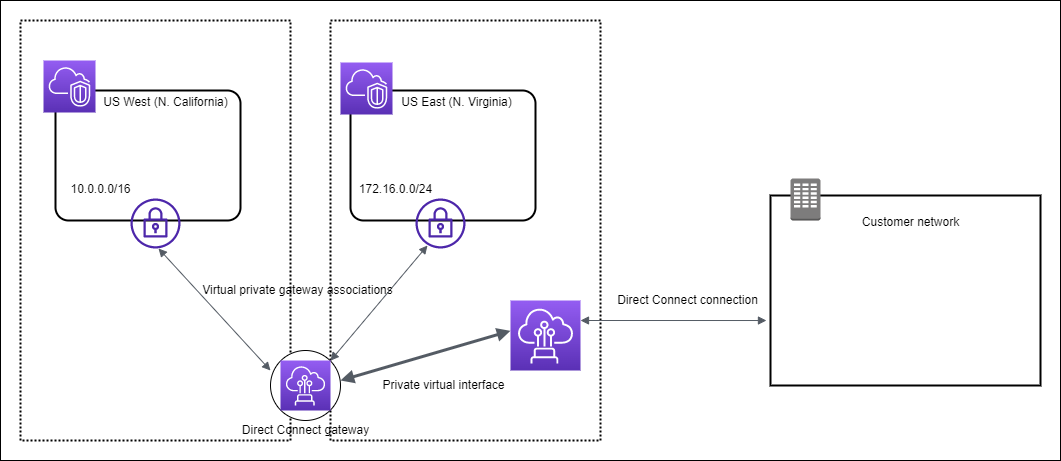
Direct Connect Gateway:
- Use AWS Direct Connect gateway to connect your VPCs. You associate an AWS Direct Connect gateway with either of the following gateways:
- transit gateway when you have multiple VPCs in the same Region
- virtual private gateway (VPG)
- transit gateway when you have multiple VPCs in the same Region
- virtual private gateway (VPG)
- Need only one Private VIF to connect to the Gateway – rather than a VIF for every VPC
- GLOBAL resource – can create one in any region and access it from any region
Limitations:
- Non-transitive – connected VPC’s can’t communicate over the Gateway, Connected DC’s can’t communicate over the Gateway
- Connected VPC’s can not have overlapping CIDR blocks
- Need a Private VIF to connect to the Gateway – cannot be public
- A VPC can’t connect to more than one Direct Connect Gateway via its VPG
- Same for VIF: VIF to only one Direct Connect Gateway; and VPG to only one Direct Connect Gateway
- each VGW has to be attached to a VPC – not loose
Quotas:
LAG - Link Aggregation
- Combines multiple physical connections
- A LAG is a logical interface that aggregates multiple connections at a single Direct Connect endpoint, allowing you to treat them as a single, managed connection. You can create a LAG from existing connections, or you can provision new connections.
- You can add links once LAG is defined
- Prerequisites:
- All connections need to be of same bandwidth
- Max of 4 connection in a LAG
- All connections must terminate at same AWS Direct Connect point
- Number of new connections – optional - The number of new connections that will be requested for the new LAG.
- Minimum links – optional -The number of connections that must be link-up in order for the LAG to transition to link-up.
- Direct Connect - BGP only
802.1Q Trunk:

BGP - Border Gateway Protocol
- Port 179
- BGP – IBGP (internal, within Autonomous System) and ENGP (Exterior BGP - b/w Autonomous Systems):
- path vector protocol;
exchange route advertisements; AS have peering agreements
- when you are connected
to multiple networks at the same time, then certain paths will be shorter,
faster or more reliable than others
- A unique ASN (AS Number) is
allocated to each AS for use in BGP routing.
- Routers advertise a list of
network routes over a BGP Session
- BGP does not broadcast its
entire routing table; At boot, your peer will hand over its entire table. After
that, everything relies on updates received.
Attributes:
- Shortest AS_Path - the path
which traverses the least number of AS "wins." (how many AS's i need
to pass to get to you)
- Multi_Exit_Disc (Multi-exit
discriminator, or MED) - tell a remote AS that if there are multiple exit
points on to your network, a specific exit point is preferred.
Issues:
- Routing table growth,
aggregation isn't always possible
- Concern that someone will
"advertise the Internet." - some small AS advertises its routes as
default to an large ISP; ISP distributes these routes to others - and then all
of internet traffic can be routed to the small AS. Solution - route filtering,
filters so that your routers won't accept routes from customers that you aren't
expecting (small AS)
- Flapping; BGP has a mechanism
to "hold down" routes that appear to be flaky.
Communities:
The ‘BGP community’ is an
additional information (attribute) added to prefixes, that is being advertised
to the BGP neighbors.:
- Internet: advertise these
routes to all neighbors.
- Local-as: prevent sending
routes outside the local AS within the confederation.
- No-Advertise: do not
advertise this route to any peer, internal or external.
- No-Export: do not advertise
this route to external BGP peers.
- EBGP - exterior BGP - over
internet
- iBGB – internal BGPs
BGP on AWS Direct Connect:
Inbound connections:
- Client must own the prefixes (IPs) - AWS will perform inbound packed
filtering to validate the source
- Traffic must be destined to AWS
public prefixes - no transitive routing via AWS
Outbound connections:
- All AWS public ranges in all regions are advertised
- AS_Path is advertised
- AWS Direct Connect is automatically preferred by AWS over VPN when
attributes are similar
- Multiple AWS Direct Connect
connections with similar attributes can be used for load balancing-
- Prefixes with minimum path length of 3 are advertised
- All public prefixes with No_Export are advertised
- Route Tables on VPC - cannot configure Target as Direct Connect.
There is VGW in the middle, on the edge of the VPC, that servers as the Target
No comments:
Post a Comment